Containerization: Deep Dive into Linux Cgroups and Namespaces
In our previous article, we explored the evolution of deployment strategies—from physical machines to virtual machines (VMs) and finally to containerization. We established that containers are lightweight, scalable units that share the host’s operating system.
But how exactly does that work?
When people talk about containers, they almost immediately think of Docker. While Docker is the company that popularized the technology and made it accessible, they didn’t invent the underlying concept. The truth is, containers are purely a Linux concept that existed long before Docker. Docker simply built excellent tooling on top of existing Linux primitives.
To understand containers, you have to understand a bit of Linux architecture. In Linux, the philosophy is that everything is a file. Whether it’s memory, CPU, or a network socket, it is represented as a file.
The core idea behind containers is simple: How do we group certain processes running within the Linux environment, order them, and assign them specific resources?
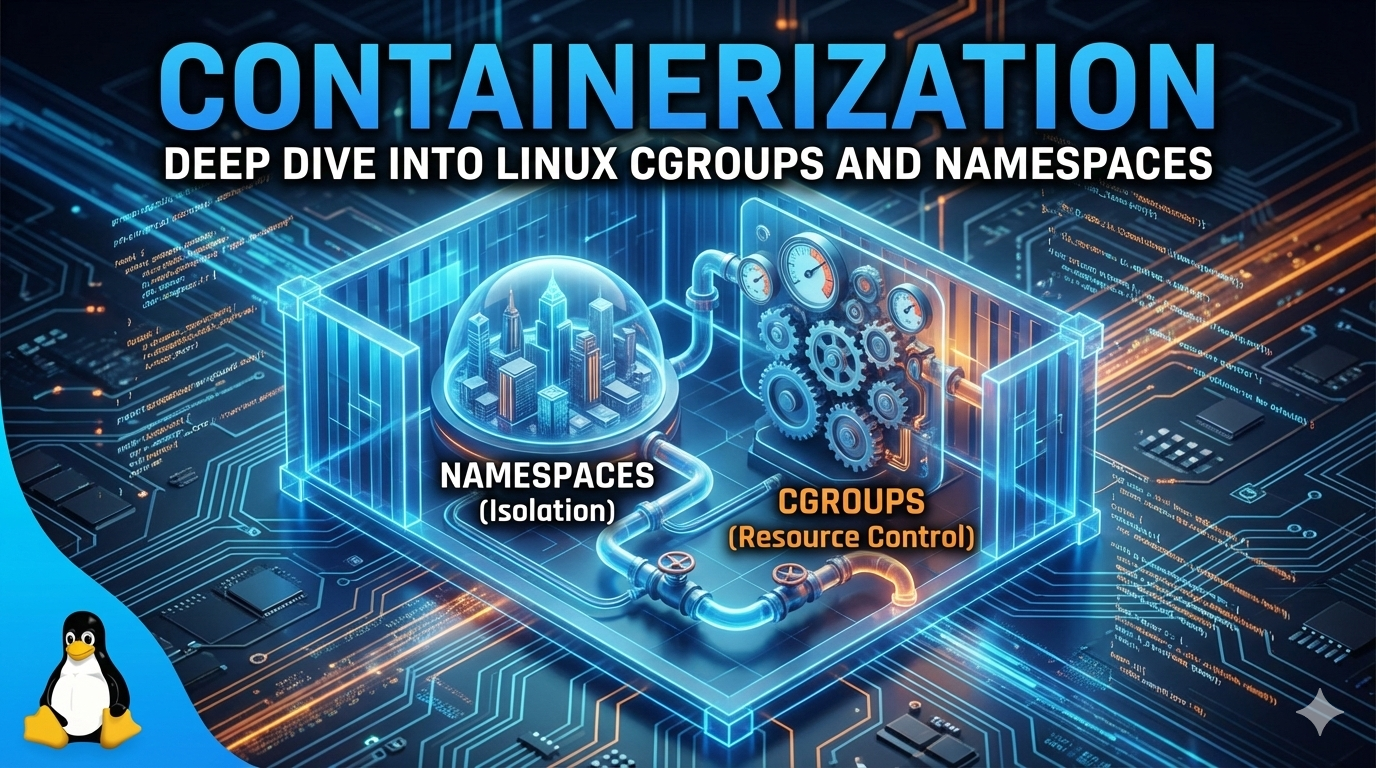
In a way, Linux itself is a giant container. All files and processes are organized into groups to either control their resource usage (CPU/Memory) or to isolate their access (Files/Network). To master containerization—and eventually Kubernetes—you need to understand the two pillars that make this possible: Cgroups and Namespaces.
1. Cgroups (Control Groups)
If processes are the workers, Cgroups are the managers.
Control Groups, or Cgroups, are a Linux kernel feature that allows you to organize processes into a hierarchy and strictly control their resource usage. In any system, processes are constantly competing for CPU time and memory. Cgroups provide a way to prioritize specific processes (like kernel processes or high-performance applications) and limit others, ensuring that a single “noisy neighbor” doesn’t crash the whole system.
How it works
Linux has several subsystems that can be controlled via Cgroups, including:
- CPU: Limits how much CPU time a group of processes can use.
- Memory: Limits the amount of RAM available.
- Block I/O: Controls input/output access to storage devices.
- PIDS: Limits the number of discrete processes.
- Network Priority: Prioritizes network traffic.
When a process joins one of these subsystems, it is placed under a specific control group that dictates its limits.
Key Functions of Cgroups
- Organize Processes: It creates a structured hierarchy for system processes.
- Telemetry & Accounting: It monitors resource usage, gathering data on how much CPU or memory a container is actually using.
- Limit & Prioritize: It enforces hard limits. For example, if you give a container 512MB of RAM, the kernel ensures it cannot exceed that amount.
Integration with Containers:
Container runtimes like Docker and Kubernetes rely heavily on Cgroups. When you run a Docker command with flags like –memory=”1g” or –cpus=”2″, Docker is simply instructing the Linux kernel to create a Cgroup for that container with those specific limits.
2. Namespaces
While Cgroups control *how much* of a resource you can use, Namespaces control what you can see.
In the world of Virtual Machines, isolation is achieved by creating completely different environments (new OS, new kernel). In Linux containers, we don’t duplicate the kernel; instead, we use Namespaces to create “views” or partitions of the system.
Namespaces deceive the process inside the container into thinking it has its own independent operating system. It hides changes made inside the container from the rest of the host system and restricts the container’s ability to see or signal processes outside its own little bubble.
Examples of Linux Namespaces
- PID Namespace: Isolates process IDs. A process might be PID 1234 on the host, but inside the container, it thinks it is PID 1 (the root process).
- Network Namespace: Gives the container its own network stack (IP address, ports, routing table), separate from the host.
- Mount Namespace: Isolates the filesystem mount points. The container sees a completely different file structure than the host.
- User Namespace: Maps user and group IDs. A user might be “root” inside the container but a regular, unprivileged user on the host.
- IPC Namespace: Isolates Inter-Process Communication, preventing containers from reading each other’s shared memory.
Key Functions of Namespaces
- Isolation Mechanism: It creates a logical wall around the resources.
- Visibility Control: Changes to resources (like files or network settings) within a namespace are invisible to the rest of the system.
- Resource Mapping: It manages permissions, deciding if an application can access a specific file or kill a specific process.
Conclusion
To summarize, a container is essentially a standard Linux process that has been:
- Constrained by Cgroups (so it doesn’t eat up all your CPU/RAM).
- Isolated by Namespaces (so it can’t mess with other processes or the host files).
Understanding these two concepts is critical because they are the building blocks of modern infrastructure. As we move forward to discuss Kubernetes, you will see that K8s is essentially an orchestration engine that automates the management of these Cgroups and Namespaces at a massive scale.






Post Comment